Traditionally, ransomware attacks are seen to hit local drives (endpoints), but the trend might get shifted now. Cloud storage is long termed as a safe storage drive from ransomware attacks, but the research by Proofpoint is ringing the threat bell.
Researchers from Proofpoint have discovered a feature in the Microsoft 365 suite that could be misused to encrypt files stored on OneDrive and SharePoint. In fact, the ransomware attack would be so strong that you will not be able to recover files without dedicated backups or decryption keys from the attackers. So, let’s explore more about this ransomware attack on OneDrive and SharePoint files. But first, let’s take a brief look at ransomware.

Ransomware – Quick Overview
Ransomware is one of the malware types that takes the control of the victim’s system or account to block access and also encrypt the data. There are many ways for ransomware attackers to penetrate the victim’s system. The most popular way is the phishing approach in which the victim is tricked to share login details or click a malicious link/file that then installs the malware in the system. Alternative, system loopholes can also be used to penetrate the user’s system/account.
Once ransomware attackers are successful in penetrating the system, they can do a lot of activities, i.e., block access, encrypt data, mine cryptocurrencies, etc. In most cases, attackers encrypt the data and then ask for a ransom fee to decrypt the data. Moreover, many attackers even offer a discount for early payments so that the victim doesn’t think much and pays the ransom quickly. In addition, attackers also provide a complete step-by-step guide on how the victim can complete the transaction.
New Vector – Now your Files in OneDrive and SharePoint can be Locked
Proofpoint has identified a dangerous feature in Microsoft 365 that empowers ransomware attackers to encrypt the OneDrive and SharePoint files in the compromised users’ accounts. Afterward, the files could only be accessed back by paying for the decryption key or recovering the dedicated backup made beforehand.
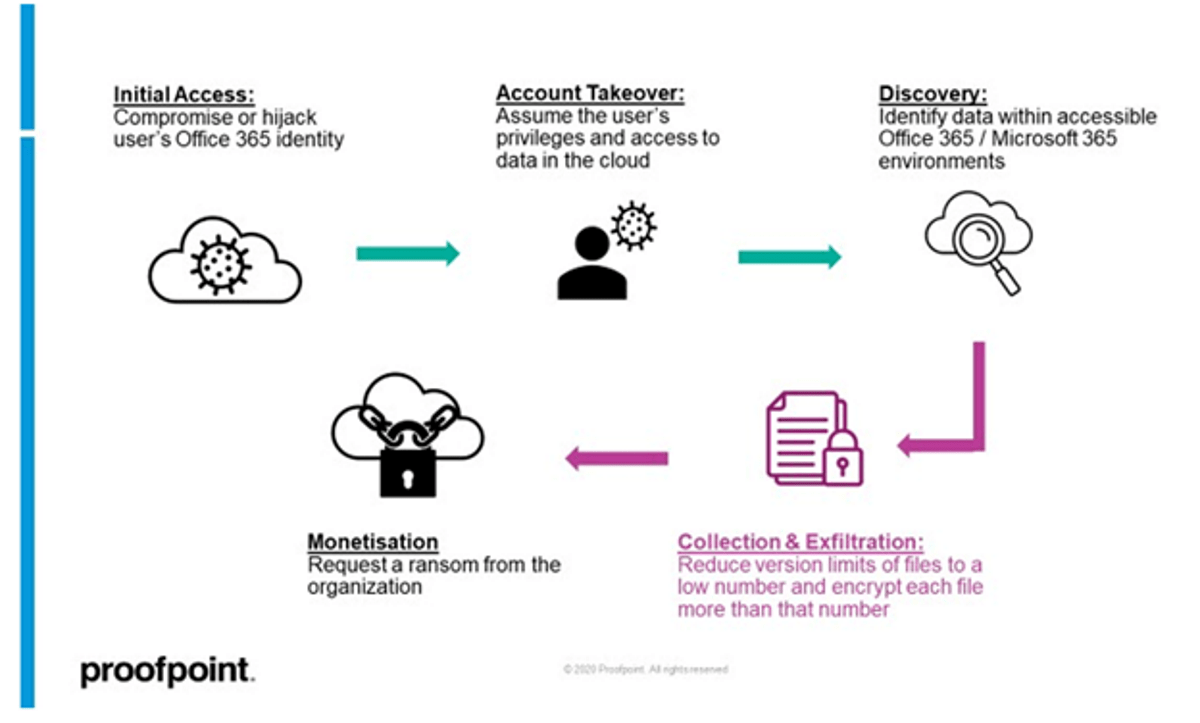
The research by Proofpoint indicates the “AutoSave” feature of Microsoft 365 as a potential threat. This feature is meant to make copies of older versions of files stored on OneDrive/SharePoint. The attack chain as pointed out by Proofpoint could go as follows:
Initial Access
Attackers start by first gaining access to the user(s) OneDrive or SharePoint account(s) through compromising login credentials, tricking the victim to allow third-party OAuth apps, or hijacking the web session of a logged-in user.
Account Takeover
After successful penetration of the user account, attackers have access to all the files stored by the user in OneDrive or SharePoint.
Collection and Exfiltration
Reduce the version limit of files to a low number, like “1” and then encrypt the file more times than the version limit, i.e., encrypt the file twice if the version limit is set to 1. Besides that, attackers can also do a double extortion tactic by exfiltrating the encrypted files.
Monetization
Once the original versions of the files are lost and the encrypted versions are left in the user account, the attackers can then ask for a ransom to decrypt the files.
All the above steps can be automated using Microsoft APIs, PowerShell scripts, and command line interface scripts.
The document library in OneDrive and SharePoint is based on multiple attributes, where one attribute is the number of saved versions that the user can change. When a user reduces the document library version limit, it means that new changes in the file will make older versions quite difficult to restore.
So, what attackers can do is they can either create so many file versions or change the limit of the version to just “1” and then encrypt every file more times than the version limit. For example, the default version limit in most OneDrive accounts is 500. So, attackers can edit document library files 501 times. This way, the original version of every file is the 501st version file, which is no longer accessible. Alternatively, they can set the version limit to 1 and then encrypt the file twice.
What to Do if You Get Hacked and They Ask for Ransom?
From the above research work of Proofpoint and the vulnerable “AutoSave” feature of Microsoft 365, there are clear signs that ransomware attacks can occur in your cloud storage. When this vulnerability was discussed with Microsoft by Proofpoint, Microsoft stated that the older versions of files can be recovered by an additional 14 days through the help of Microsoft Support. However, Proofpoint did follow that but failed to restore older versions.
So, if you get a victim of a ransomware attack and your data is encrypted in your cloud account or local drive, then the one quick option is to pay the ransom and get the decryption key. But this approach is not recommended because you never know if the decryption key would work, you will get back the data, or the attacker might demand more money. Moreover, it also encourages attackers to do more such attacks.
The recommended steps you should immediately perform after the ransomware attack are as follows:
- Disconnect and isolate the infected device.
- Contact your local authorities.
- Reach out to a cybersecurity expert to try to remove malware.
- Look for the data backup you might have created beforehand or try to restore data from others if you have shared it with them.
In short, you should try every possible measure that you can take to retrieve data without paying the ransom.
Ways to Store Files Securely (on your PC)
Ransomware and other cyberattacks are a serious concern today. As per Cybersecurity Ventures, cybercrimes will cost the world $10.5 trillion annually by 2025. So, it is important more than ever that we store our data and files securely. Below are some of the effective ways to store files securely on your PC:
- Encrypt files/folders in Windows. To do that, right-click the file/folder and then click Properties > Advanced > Encrypt contents to secure data > OK.
- Control the access to your files/folders in Windows. To do that, right-click the file/folder and then click Properties > Security > Edit. Afterward, select the user’s name or group and then click “Deny Access”. This way, the user/group will have to enter an administrative password to access that file/folder in the future.
- Use third-party tools to encrypt sensitive files/folders.
- Make regular backup of your files in the cloud or external hard drive.
- Use antivirus software.
- Keep your operating system and software up-to-date and patched.
- Avoid giving administrative access to all software.
To sum up, you should deploy every possible measure you could take to secure your files on your PC. These measures do not guarantee complete protection from cyberattacks, but they can minimize the chances greatly.